Cyber Security Architecture Diagram for IT Security Company
Having solid network security architecture is a foundational need for any security organization’s success. Together with our client, we developed an cybersecurity architecture design tool to secure and scale the enterprise software development life cycle.
The solution visually reflects the network security architecture and all actions undertaken to protect it from cyber attacks.
| Client | Cybersecurity company |
|---|---|
| Business need | website architecture diagram, user journey flow diagram |
| Scope | design, UI/UX, interactive mockups |
| Technology | GoJS |
How Cyber Security Architecture Diagram Works?
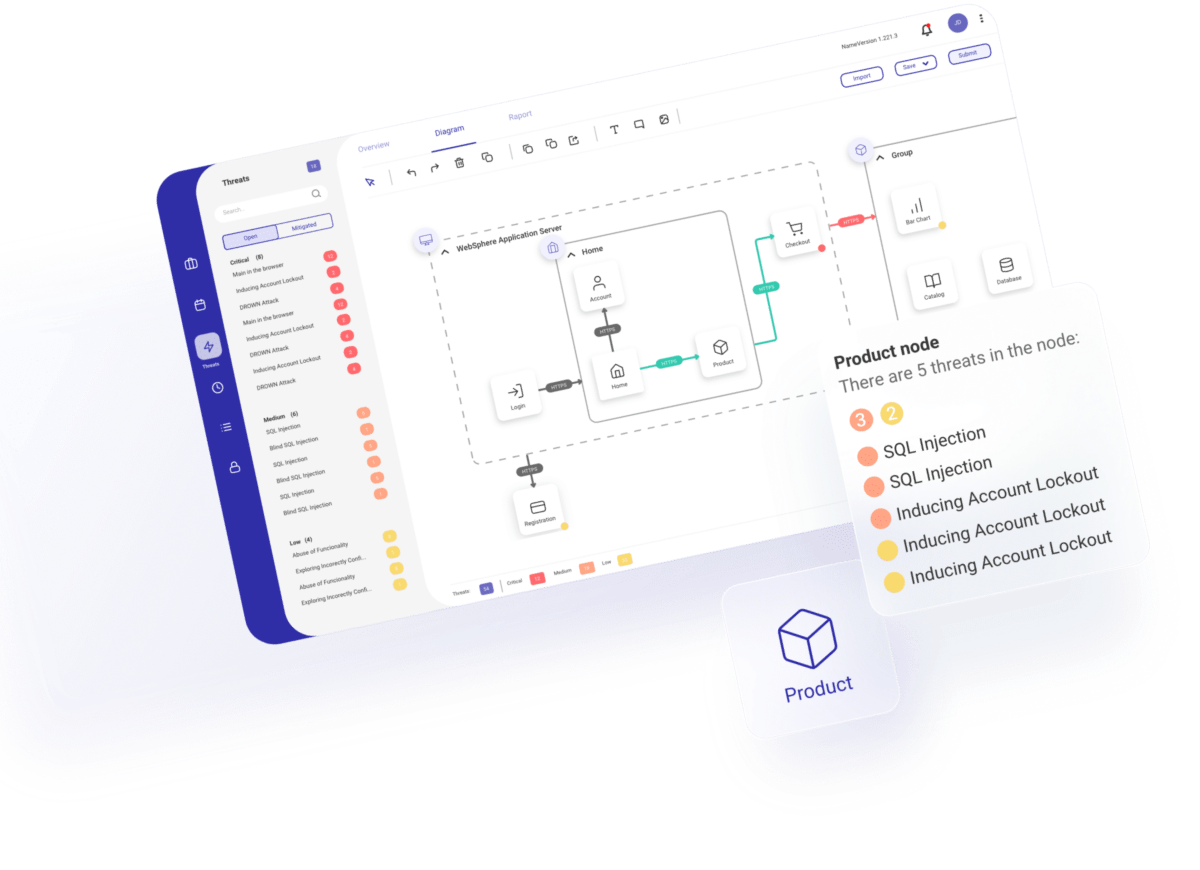
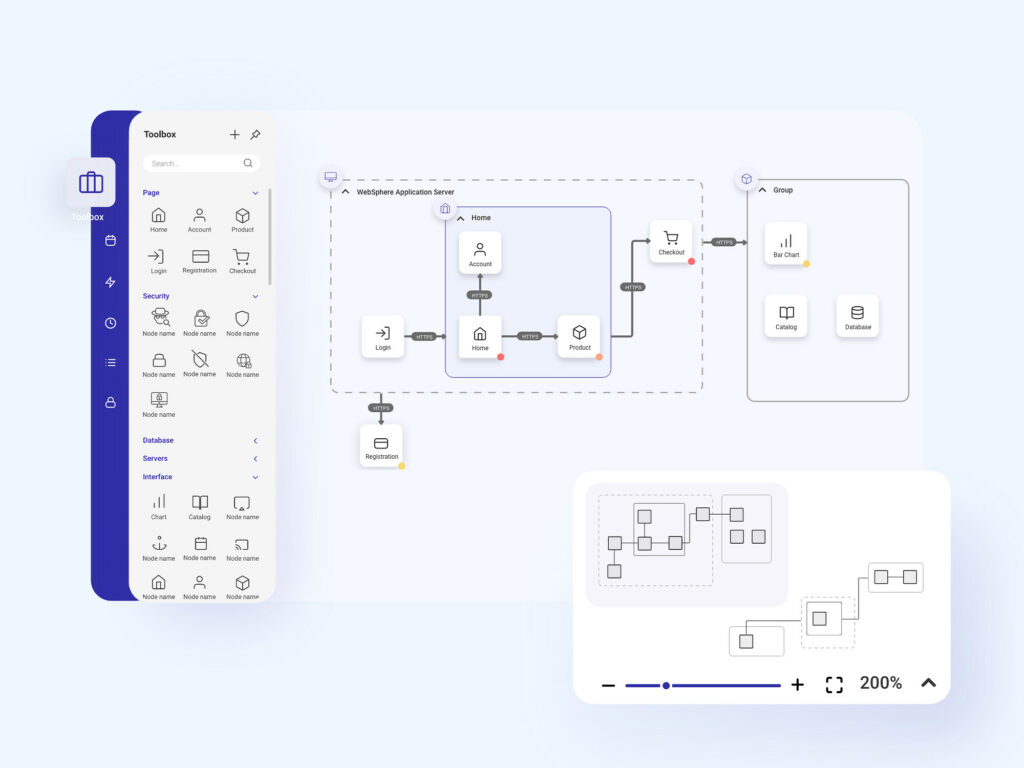
Security Architecture Overview
A powerful tool that allows you to place thousands of pages
on a security network diagram. By collapsing the content, the user can view the
site map. With a double-click on a node, it breaks down into a
group of related subpages.
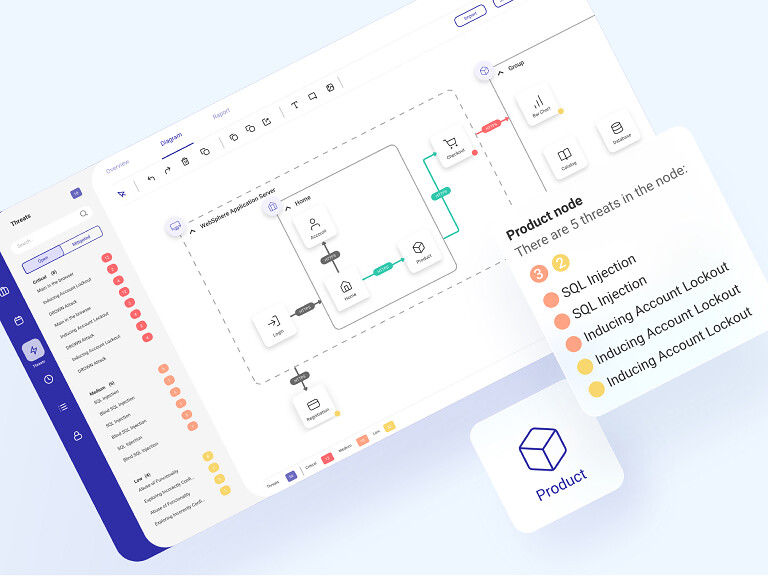
Cyber Security Architecture Diagram with Threats Map
A well-done network security architecture results in displaying
appropriate types of threats, signaled by three-level criticality alerts. Depending on the website, the map indicates potential hacker attacks. It prevents capturing screenshots of the websites or anonymizing the CVV code.
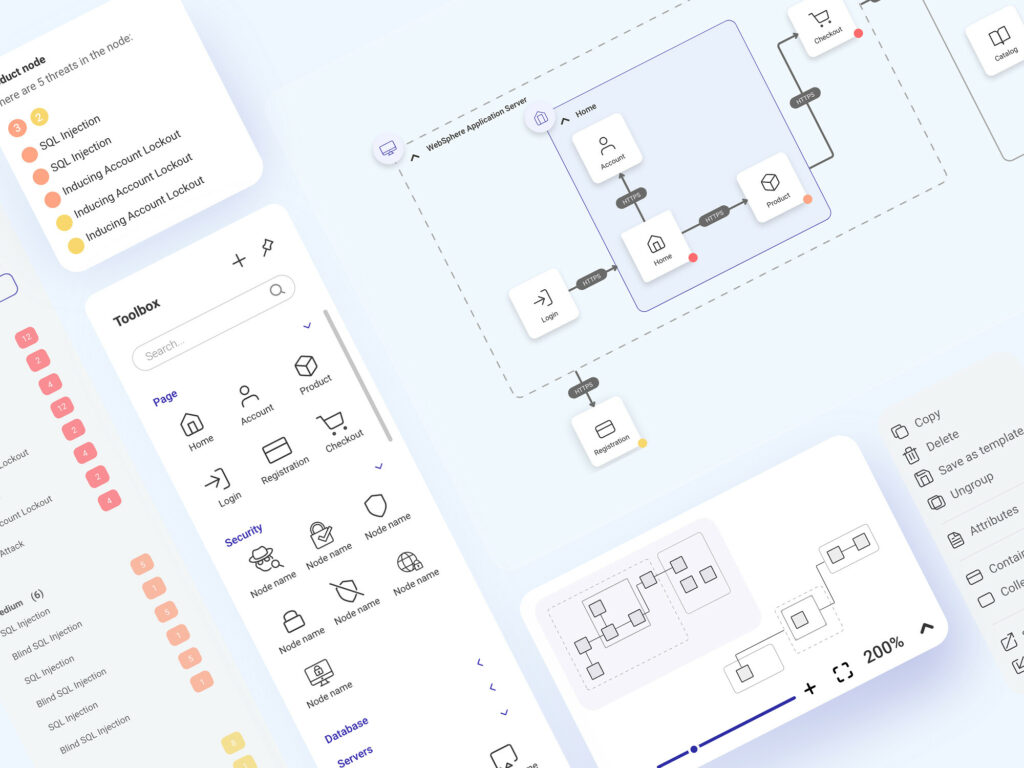
Cyber Security Architecture Diagram with Threats Modeler
When selecting the beginning and end element of security network diagram, the tool colors
the connections and informs about the occurring threats. For
large systems, it is helpful to zoom out and focus on the most
endangered path.
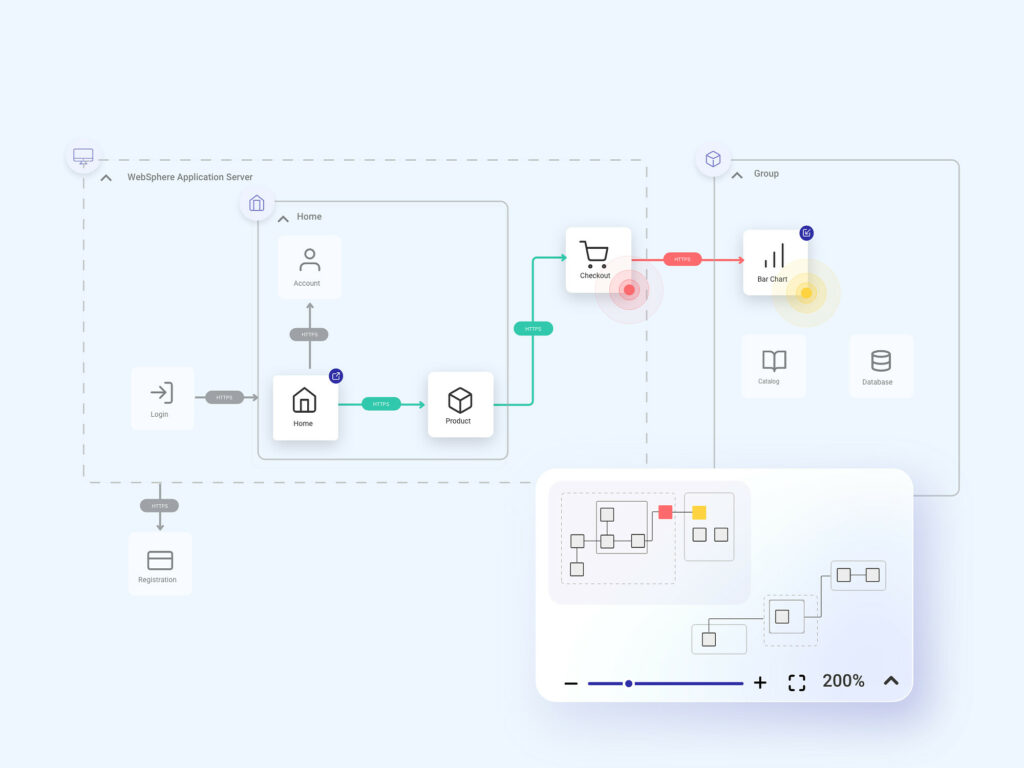
Cyber Security Architeture Diagram with Mini Map
The view includes a minimized map that allows for smoother
navigation through the website’s cybersecurity architecture. Connections
between nodes can take different colors depending on the
user’s journey.
Cyber Security Architecture Diagram Enables Understanding Your Organization’s Software Architecture
The cybersecurity architecture design tool secures and scales the enterprise software development life cycle and ensures solid network security architecture. The solution uses drag-and-drop feature to build security architecture diagrams that visually supports and reflects the network’s structure.
The interactive components enable the users to detect and protect the network from cyber-attacks. The tool ensures focusing on the user’s journey flow and the possible threads appearing while operating.
Cyber Security Architecture Diagram’s Benefits
Drag and drop feature to accelerate and simplify security architecture diagram’s buidling
Intuitive user interface enabling easy navigation
Ready to design the large IT security architecture diagrams